Note: This article is specifically targeted at Windows computer, but the security issues could happen to any OS as well.
1. Vulnerabilities in Plugins

Your browser, even “out of the box,” uses a number of plugins to add extra rendering capabilities on websites you visit. In Firefox, you can view these plugins in the Tools -> Add-ons -> Plugins” section. These plugins are generally fine, but some of them are poorly coded and open holes in your browser’s security that it has not anticipated. The Java plugin is a perfect example of a vulnerable module. Java’s interpreter itself is prone to very nasty vulnerabilities that allow hackers to infiltrate your computer and post updates on social media sites on your behalf.
How to protect yourself:
There are two things you can do: keep all your plugins up to date and delete any plugins you don’t absolutely need. I need not mention how difficult it is to keep 100 plugins up to date. It’s better to look after five or ten of them. This applies to the addons and extensions as well. (Note that in Firefox, plugins and addons are not referring to the same thing)
2. Being conned to download unwanted software

If you have been to some sketchy download site, you would have seen cases where it try to convince you to download (and install) a software before you can download their stuff. They put fake download buttons on their pages leading to other sites that offer a “downloader application” to get your file. They convince you that you need this application in order to gain access. Once you run it, you are met with an unpleasant surprise. Sometimes the application doesn’t work at all but installs a virus in your computer. Other times it works, but installs a service that spies on your personal information.
How to protect yourself:
Look carefully at sites showing you more than one button for the same action. Be mindful of what you see on the Web and exercise scrutiny. If the website doesn’t have a strong positive reputation, don’t trust it. Search the website’s URL surrounded by quotation marks on Google. See what other people say about it.
And if you have downloaded the software, run a anti-virus/anti-malware test before you install it. If you do decide to install it even though you are not very sure about it, do a backup of your system first.
3. Toolbars

When you install software, it sometimes sneaks into a dialog where it asks you if you want to install a toolbar (and that’s when it’s playing nice). This is the most common way in which people are duped into installing browser toolbars that mess with their computers. This kind of software relies on a psychological flaw, namely the fact that people have a general tendency to click “Yes” and “Next” and skip over installation steps in their impatience. It happens even to the best of us.
Toolbars are sometimes inoffensive, but many times, they can be just as bad as viruses. Some of them set your homepage and search provider as they see fit while not letting you disable this or uninstall them. Others grab your keyboard input and steal your passwords and other confidential information. Since you use your browser to log in to web-based services and authenticate your card data, it’s very obvious that a toolbar like this can be extremely dangerous to your privacy. Although such malware is not very common nowadays, it still poses a significant threat to users who are easily absent-minded during software installations.
How to protect yourself:
These toolbars tend to be very difficult to get rid of, so the best way is to observe your installations carefully everytime you run an installer.. If you’re installing a program and it asks you to install a toolbar, refuse wherever possible. If it’s not possible to refuse, do not install the application. There are always alternatives out there that are more worth your time. Remember always to keep your anti-virus up to date. Most antivirus software can efficiently detect malware that’s found in toolbars and get rid of it, even if you can’t. Don’t forget to try to stick to sites that are reputable rather than Internet back-alleys to download your stuff.
4. Native Browser Vulnerabilities

There are plenty of browsers out there and some of them come with unintended security vulnerabilities. If you (or your company) are still stubbornly using IE 6 and 7, or even 8, as your primary browser, you are basically inviting the hackers to attack you. Even a popular browser like Chrome also has security issues, namelycross-site scripting (XSS), that make it vulnerable to attack.
How to protect yourself:
There is nothing much you can do except to wait for the browser’s developer to patch up the security loophole. Thus, you should always upgrade your browser to the latest version so new fixes to vulnerabilities will automatically be installed. In addition, make sure you exercise care and vigilance when browsing the web, even with the most secure and most updated software.
Questions?
If you have any questions, do not hesitate to leave a comment below! Also, don’t forget to let other readers know what useful tips you have to keep your browser safe!



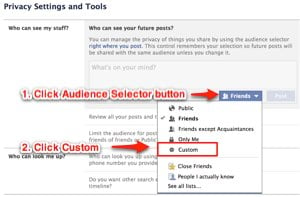 The easiest way to deal with a snoop is to limit their access to your profile, posts, and albums. Doing so takes only a minute.
The easiest way to deal with a snoop is to limit their access to your profile, posts, and albums. Doing so takes only a minute.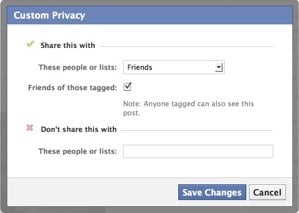 Okay, so maybe the person isn’t nosy enough that you need to block access completely – you’d just prefer him or her to not see one specific post about playing hooky, for instance. No problem. Just click the button immediately to the left of the blue “Post” button when typing a status update. Just like using the Privacy Settings page, you can choose to block individual people from seeing the post using the “custom” option. Think of it as giving your boss a brief social timeout.
Okay, so maybe the person isn’t nosy enough that you need to block access completely – you’d just prefer him or her to not see one specific post about playing hooky, for instance. No problem. Just click the button immediately to the left of the blue “Post” button when typing a status update. Just like using the Privacy Settings page, you can choose to block individual people from seeing the post using the “custom” option. Think of it as giving your boss a brief social timeout.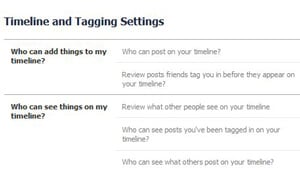 Sometimes it's not your posts that are the problem, it's what your friends are posting. To limit the person's access to what others post on your timeline, got to the Privacy Settings page and select Timeline and Tagging. There you can choose "Who can see what others post on your timeline." You can also limit "Who can see posts you've been tagged in on your timeline."
Sometimes it's not your posts that are the problem, it's what your friends are posting. To limit the person's access to what others post on your timeline, got to the Privacy Settings page and select Timeline and Tagging. There you can choose "Who can see what others post on your timeline." You can also limit "Who can see posts you've been tagged in on your timeline."